|
An adaptive security system provides the means to intervene in the working of the system at any time. Such an intervention can either be triggered automatically or by human intervention from the management console.
Consider the following situation. A network monitor detects a ping flooding attempt from a machine outside the organization's network. The central management system is informed of this attack and decides to prevent all traffic originating from that source to enter the network. It contacts the firewall and tells it to update its filtering rules to deny all traffic from the attacker's source address.2.3
In this case the firewall is the decision enforcement application because it sits immediately at the place where the decision taken by the management system is to be enforced.
As with the monitor application, information can be transferred by polling or by signalling. In this case however the central management service signals the enforcement application rather than the other way around. Alternatively the enforcement application polls the central manager to see whether it has to enforce a a particular decision.
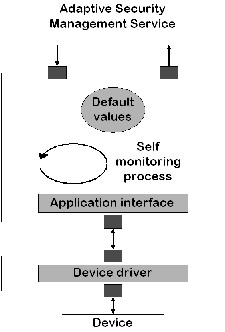
Like the monitoring application, the decision enforcement application needs to be fail-safe and autocorrective. Part of the application consists of a monitor that continuously checks the system for potential errors. In case an error occurs, the system has to switch to a default configuration and inform the management system of its malfunction and the decision it has taken. This would also be the case when the enforcement application notices a communication problem with the central management system. Such a failure can also be identified in either of two ways described above, by polling or by signalling.
In the case of polling the central management system checks regularly with the decision enforcement application to see whether it is still ``alive''. The enforcement application notices this, stores the time at which it has been polled and returns a message to the central management system with the timestamp for logging purposes. If the time expires at which it is supposed to be polled, it can decide to change its settings to some default value. This system can inform both the enforcement application and the central system about a communication failure.
In the other case the initiative originates from the decision enforcement application itself. It sends a message to the central manager (a signal or interrupt) to say it is still there. If it does not get an answer, it switches to its default setting. If the manager application does not get an interrupt from time to time, it generates an entry for the log and polls the enforcement application for its presence or takes other action.
The decisions that are taken autonomously by the enforcement application can become more exacerbated as the failure persists. A firewall can first deny all traffic intended for the most vulnerable services, and later decide to cut off all incoming and outgoing connections.
The
above
discussion
already
indicates
that,
much
like
the
monitor
application,
the
enforcement
application
needs
two
interfaces
with
the
central
system
-- one
for
sending
and
one
for
receiving --
and
an
interface
that
actually
forces
the
device
into
its
new
state
(see
also
figure
2.3).