



Next: 2.1.4 The security definition
Up: 2.1.3 The central security
Previous: 2.1.3 The central security
2.1.3.1 The
knowledge
base
A
basic
stripped-down
framework
for
a
dynamic
security
system
would
consist
of
a
monitoring
module,
an
analysis
module
and
a
response
module.
We
now
concentrate
on
the
inputs
that
allow
the
analysis
module
-- the
security
service
manager --
to
do
its
reasoning.
In
this
context
it
is
important
to
note
that
we
have
made
the
assumption
that
all
our
resources
-- our
network,
the
computer
systems,
our
premises --
are
not
necessarily
100%
safe,
either
because
they
are
inherently
insecure
or
because
we
have
chosen
not
to
secure
them
for
cost-efficiency
reasons.
It
is
still
the
task
of
the
security
management
system
to
look
after
all
our
assets
anyway.
Previously
we
already
distinguished
between
facts
and
heuristics.
The
facts
constitute
the
information
that
can
easily
be
retrieved
about
the
environment
in
which
the
security
system
is
active
and
for
which
it
is
responsible.
Information
about
the
environment
can
be
compiled
by
scrutinizing
all
the
aspects
of
the
resources
that
the
system
protects
for
vulnerabilities.
The
factual
information
about
the
known
vulnerabilities
are
stored
in
a
vulnerability
database.
To
find
out
about
the
loopholes
in
the
organization's
defense,
scanners
are
used.
A
network
scanner
can
look
for
known
network
problems
like
insecure
webservers
and
a
computer
scanner
can
check
workstations
and
servers
for
known
vulnerabilities
like
operating
system
weaknesses
and
bugs.
The
output
of
the
scanners
is
stored
in
a
database
in
a
format
that
the
security
engines
can
handle2.5.
This
procedure
has
to
be
repeated
regularly
as
the
configuration
of
our
internal
network
and
its
machines
is
bound
to
change
over
time.
New
machines
are
added,
software
is
installed
to
provide
new
services
to
users
in-
or
outside
the
corporate
network,
existing
software
is
upgraded
and
so
forth.
Moreover,
the
list
of
known
vulnerabilities
also
grows
over
time
as
specific
software
becomes
more
widely
used
and
more
bug
exploits
are
reported.
Users
change
default
configurations
and
try
to
get
around
annoying
existing
security
measures,
for
instance
by
installing
their
own
modem
dial-up
connections.
The
database
should
therefore
be
updated
frequently
and
automatically.
This
is
shown
in
figure
2.4.
Figure 2.4:
Collection
process
of
static
data
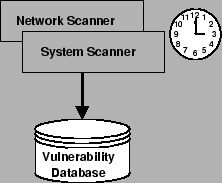
|
This
way
the
adaptive
security
system
supports
and
facilitates
change
management.
Apart
from
the
factual
information
we
also
need
to
represent
the
security
experts
knowledge
and
create
a
set
of
heuristics
that
warn
the
organization
about
dangerous
activity
on
its
network
or
computers.
A
risk
analysis
will
tell
what
is
considered
dangerous
activity
and
what
expertise
is
both
needed
and
wanted2.6.
A
risk
analysis
identifies
the
vulnerabilities
within
a
pre-established
review
boundary.
The
inference
engine
addresses
these
vulnerabilities
by
analysing
input
from
the
monitors
and
looking
for
rules
that
tell
it
how
to
activate
a
countermeasure.
The
selection
of
appropriate
countermeasures
for
a
given
situation
is
part
of
the
expert's
knowledge.
What
set
of
rules
is
available
to
the
inference
engine
depends
on
the
outcome
of
the
risk
analysis
phase
and
is
reflected
in
the
security
policy
documents.
The
security
policy
reflects
the
attitude
of
the
management
towards
security
and
indicates
what
measures
have
been
taken
to
safeguard
the
organization's
assets.
For
example:
an
organization
that
has
decided
to
connect
to
the
Internet
may
understand
that
this
entails
certain
security
implications.
In
this
case
the
network
security
policy
and
related
documents
will
contain
statements
about
how
the
network
is
to
be
used
and
what
is
to
be
considered
an
abuse
of
resources.
A
specific
rule-base
containing
the
appropriate
rules
would
then
assist
the
inference
engine
that
watches
for
suspicious
activity
on
its
corporate
network.
Table 2.2:
expert
and
procedural
logic
in
an
adaptive
security
management
system
| expert
logic |
procedural
logic |
| analysis
and
selection
of
a
countermeasure |
activating
the
countermeasure |
|
There
is
even
more.
The
ultimate
knowledge
based
system
goes
further
than
analysing
and
deciding.
If
at
all
times
the
logs
reflect
the
state
of
the
system,
this
enables
the
security
management
service
to
learn
from
previously
taken
decisions.
All
the
decisions
and
factors
that
lead
to
a
decision
are
logged
through
the
logging
and
auditing
application.
The
logs
provide
feedback
that
can
help
the
inference
engine
with
future
decisions.
Remember
that
rule-based
systems
use
heuristics
to
get
to
a
conclusion,
not
clear-cut
algorithms.
Clearly,
if
this
decision
has
afterwards
proved
to
be
ineffective,
more
information
was
required
to
make
a
correct
decision,
or
a
wrong
reasoning
has
been
followed.
The
knowledge
based
system
is
therefore
capable
of
``learning''2.7.
This
illustrated
in
figure
2.5.
Figure 2.5:
The
knowledge
based
system's
rule-base
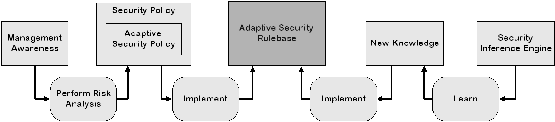
|
Footnotes
- ...
handle2.5
-
Footnote:
ideally
this
would
be
an
open
standard
format
like
SQL
-
"What
do
you
mean,
is
there
an
SQLstandard
?
-
Oh,
plenty!"
- ...
wanted2.6
-
I.e. is
perceived
to
be
cost-effective.
- ...
``learning''2.7
-
In
the
field
of
artificial
intelligence
the
term
``knowledge
based
system''
is
often
reserved
for
systems
that
are
capable
of
inferring
new
knowledge
from
previously
taken
decisions,
as
opposed
to
simple
``rule-based''
systems
that
only
use
a
predefined
set
of
rules.




Next: 2.1.4 The security definition
Up: 2.1.3 The central security
Previous: 2.1.3 The central security
(c) 1998, Filip Schepers
