As we already argued, a comprehensive security system could provide one management console that interacts with many security systems that are different in nature, like network security, computer security and physical security. It would therefore be unrealistic to try and define a single interface that defines all possible interactions between all possible peripheral systems. A different approach would be to set systems up according to a two-tier model, with back-end processors that plug into the central management system and front-end processors that handle communication with the peripheral application or device.
The
back-end
processors
that
are
known
to
the
KBS
can
be
listed
in
a
functionality
table.
They
contain
information
about
the
functionality
of
the
peripheral
device
or
application
they
serve.
They
know
the
format
of
the
messages
(order
of
fields,
contents
of
fields,
data
types,
etc.)
they
use
to
communicate
with
their
associated
front-end
processors.
The
communication
between
the
central
management
system
(i.e. the
KBS)
and
the
peripheral
applications
via
the
back-
and
front-end
processors
can
be
bidirectional
and
involve
processors
from
various
applications.
We
will
refer
to
these
applications
as
peripheral
applications
because
they
are
addressed
indirectly
through
the
API
and
the
processors
and
because
we
located
them
at
the
periphery
of
our
drawing
of
an
adaptive
security
system
(figure
2.1
on
p. ![]() ).
).
Typically
a
monitor
application
would
use
its
front-end
processor
to
send
a
message
to
the
central
management
system
via
its
associated
back-end
processor.
Under
certain
circumstances
the
inference
engine
of
the
expert
system
might
require
additional
information
-- depending
on
the
rule
that
is
being
fired
from
the
rule
base --
in
order
to
take
a
decision.
It
will
scan
the
functionality
table
for
the
back-end
processor
it
should
contact
and
inform
it
about
the
type
of
data
it
needs.
The
selected
processor
will
translate
the
request
into
a
message
to
be
sent
to
the
front-end
processor
of
the
peripheral
application.
The
communication
subsystem
forwards
the
message.
At
the
other
side,
the
requested
information
is
gathered
and
sent
back
to
the
back-end
processor.
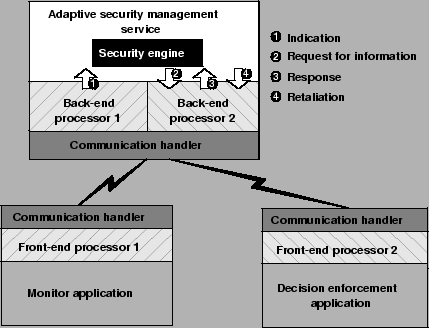
This
is
shown
in
figure
2.6.
|
The KBS might also want to indicate the quality of service (QOS) required in terms of maximum response time or confidentiality for instance, thereby indirectly specifying a communication medium to be used like a network or a direct cable connection. The QOS field can be ignored by the back-end processor but it is of value to the communication handler. The front-end processor remembers what channel was used for the request and send its response using the same channel2.10.
Other communication issues include: