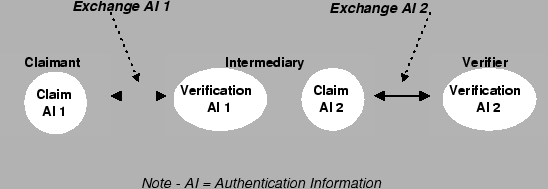
|
Consider
the
case
where
two
organizations
want
to
cooperate
in
a
given
project.
Internally,
both
organizations
use
different
authentication
mechanisms.
A
subject
(the
claimant)
of
the
security
domain
``Fish
Ltd.''
wants
to
engage
in
an
authenticated
conversation
with
a
subject
(the
verifier)
from
domain
``Chips
Inc.''.
The
authentication
service
from
domain
``Fish''
may
then
function
as
an
intermediary
to
vouch
for
the
claimant
according
to
an
in-line
authentication
model
(see
figure
3.3,
[MIT98, p.2-14]).
The advantage over using an authentication service without the adaptive security framework is that now the security system can supervise the outgoing connections originating from the inside network and enforce the security policy. The authentication server could ask the adaptive security management service if the authenticated conversation is allowed. The security management service's inference engine would fire the appropriate rules to see in which circumstances the communication is allowed and dynamically abort the conversation if the circumstances change.