|
In order to manage the risks an organization is confronted with, you have to identify what these risks are, where your vulnerabilities lie, what the impact of a threat can be and what the chance of the occurrence of a threat is. You would look for the best balance you can get between the cost of security and cost of insecurity to achieve sustainable profit making. It means you continuously have to make compromises: you are willing to accept levels of risk provided that you believe you can manage those risks. Undertaking a risk assessment however is not a trivial exercise due to the difficulty of measurement.
The cost benefit of an information security solution is determined by two factors: the cost of a failure and the cost of putting countermeasures in place. The more energy you spend on appropriate countermeasures, the lower the possible loss due to failures. Therefore the total cost of security will be obtained by totalling up these two cost factors. Assuming that more effort means higher expenditures on countermeasures and smaller subsequent losses due to security breaches, functions that show the cost of countermeasures and the cost of security failures intersect at the level of effort that gives the optimum cost level, because that is where the total cost is minimal.
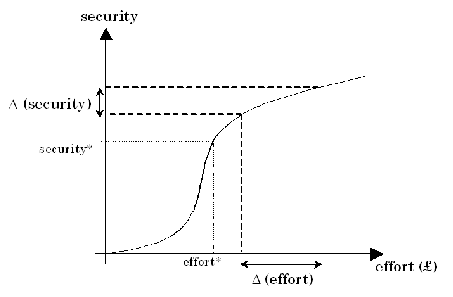
A
graph
representing
the
cost
of
security
measures
will
be
increasing
with
effort
spent,
but
until
a
certain
value
is
reached
the
relative
increase
will
be
negative,
indicating
that
it
is
possible
to
get
more
security
for
a
relatively
small
extra
cost.
Similarly,
the
function
that
gives
the
revenue7.3 of
implementing
countermeasures
shows
decreasing
returns,
meaning
that
after
a
certain
value
for
the
expenditures,
the
relative
increase
in
security
diminishes
(see
figure
A.1).
Put
differently,
all
this
means
that
the
total
cost
function
shows
increasing
costs
beyond
the
optimum
and
that
eventually
the
efficiency
of
additional
countermeasures
declines.

|