



Next: 8.2 Network security controls
Up: 8.1 General concepts in
Previous: 8.1.1 Threats in networks
In
order
to
make
it
possible
for
network
vendors
to
create
open
systems
that
can
interact,
a
layered
model
has
been
proposed
to
identify
various
services
that
networking
systems
can
provide.
This
7-layered
model
was
standardized
by
ISO
as
the
OSI
Basic
Reference
Model
ISO/IEC
7498-1.
In
the
mean
time
a
different
construct
known
as
the
TCP/IP
suite
evolved
from
the
Internet
community.
Within
these
layered
constructs
we
can
put
four
basic
architectural
levels
for
security
as
shown
in
figure
B.1
([FOR94, p.54]).
Figure B.1:
Architectural
layers
for
security
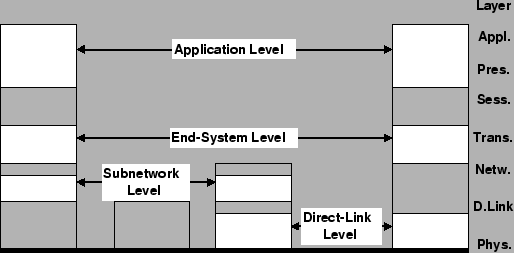
|
The
next
paragraph
gives
a
short
description
of
the
possibilities
and
some
comments
of
the
implementation
of
security
services
at
the
corresponding
level:
- Application level
- located
at
the
application
layer
or
host,
e.g. for
FTP
(file
permissions
on
remote
host)
- appropriate
in
cases
where
security
services
traverses
application
relays,
as
is
the
case
with
e-mail
(message
authentication
and
integrity)
- possibility
to
authenticate
users
(as
opposed
to
hosts)
- End-to-end level
- located
at
transport
layer
(TCP/UDP)
and/or
network
layer
(IP)
- often
used
for
confidentiality
and
integrity
protection
- offers
the
advantage
to
be
transparent
to
applications
- can
simplify
security
administration
- protects
lower
layer
protocol
headers
- Subnetwork level
- located
at
network
layer
(IP)
- often
there
are
more
end
systems
than
intermediate
nodes,
therefore
this
solution
may
possibly
be
cheaper
to
implement
- Direct link level
- located
at
physical
layer
- has
limited
applicability
(low
number
of
connections)
- offers
a
high
level
of
protection
at
low
installation
cost
- is
possibly
expensive
to
manage
at
link-by-link
basis
In
many
cases
a
combination
of
methods
at
different
layers
constitutes
the
optimal
solution
at
best
price
for
the
level
of
protection
required.
Risk
analysis
is
necessary
to
locate
the
vulnerable
areas
and
analyse
the
requirements.




Next: 8.2 Network security controls
Up: 8.1 General concepts in
Previous: 8.1.1 Threats in networks
(c) 1998, Filip Schepers
