



Next: 8.3.2 Network layer security
Up: 8.3 ISO transport and
Previous: 8.3 ISO transport and
8.3.1 Transport
layer
security
- Background:
- ISO/IEC
8072,
ISO/IEC
8073,
ISO/IEC
8602,
ISO/IEC
10736,
NIST
SDNS8.2
SP4
Communicating
entities
will
be
involved
in
a
security
association:
they
will
have
to
share
knowledge
on
how
to
communicate
securely
[FOR94, p.262].
This
includes
both
static
and
dynamic
attributes
such
as
the
identity
of
the
communicating
parties,
algorithms
used,
keys,
sequence
numbers,
etc.
It
should
be
noted
that
some
of
this
information
has
limited
lifetime.
A
certain
package
of
security
mechanism
information
can
be
predetermined
so
that
it
does
not
have
to
be
renegotiated
for
every
new
security
association.
Such
a
package
is
called
an
agreed
set
of
security
rules
or
ASSR.
ASSRs
should
not
be
kept
secure
and
should
therefore
not
include
certain
information.
ASSRs
include
the
numbers
indicating
the
level
of
requested
security
quality-of-service
(QOS)
used
in
establishing
a
secure
communication
channel.
The
concept
of
access
labels
can
map
onto
QOS
requirements,
e.g. ``sensitive
information''
is
expected
to
be
encrypted
using
export
allowed
DES,
while
"top
secret"
should
use
higher
grade
encryption.
TLSP
(Transport
Layer
Security
Protocol)
security
mechanisms
provided
by
SP4
include:
- Security
labels
(like
"top
secret",
"secret",
"public",...)
- Direction
indicators
(prevent
reflection
attacks)
- Integrity
check
values
- Encryption
padding
(if
required
by
the
algorithm)
- Encryption
TLSP
security
mechanisms
already
provided
by
the
transport
layer
are:
- Sequence
integrity
- Integrity
recovery
Entity
authentication
(connection
oriented
communication)
or
data
origin
authentication
(connectionless
communication)
happens
in
2
stages:
- 1.
- Security
association
establishment
using
keys
- 2.
- Entity
authentication
on
connection
establishment
or
origin
authentication
by
knowledge
of
a
key
used
in
the
packet
encapsulation
process.
Peer
addresses
are
checked
with
the
keys
used
for
the
authentication
process
in
order
to
detect
masquerade
attacks.
Security
associations
may
be
established
in
three
different
ways:
using
the
security
association
protocol
part
of
the
TLSP,
through
application
layer
protocol
exchanges
or
out-of-band.
Key
management
techniques
are
not
standardized,
but
Authenticated
Diffie-Hellman
could
be
used.
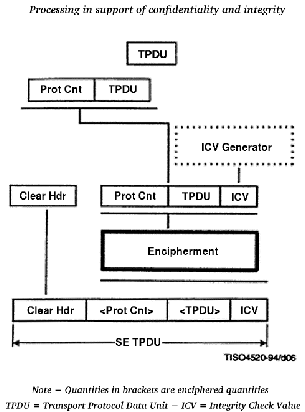
Figure
B.2
shows
the
encapsulation
process
to
provide
confidentiality
and
integrity
at
the
level
of
the
transport
layer
([ISO95, p.15]).
Figure B.2:
The
security
encapsulation
process
|
Footnotes
- ...
-
C.
Dinkel
(Ed.),
Secure
Data
Network
System
(SDNS)
Network,
Transport,
and
Message
Security
Protocols,
U.S.
Department
of
Commerce,
National
Institute
of
Standards
and
Technology,
Report
NISTIR-90-4250,
1990.
- ...
SDNS8.2
-




Next: 8.3.2 Network layer security
Up: 8.3 ISO transport and
Previous: 8.3 ISO transport and
(c) 1998, Filip Schepers
