



Next: 8.3.3 Physical layer security
Up: 8.3 ISO transport and
Previous: 8.3.1 Transport layer security
- Background:
- ISO/IEC
8348,
ISO/IEC
8648,
ISO/IEC
8880,
ISO/IEC
11577,
NIST
SDNS
SP3
NLSP
(Network
Layer
Security
Protocol)
supports
both
end-to-end
level
or
subnetwork
level
security
services
as
depicted
in
figure
B.3
([FOR94, p.278]).
As
we
are
later
discussing
possible
implementations
for
TCP/IP
which
uses
the
connectionless
Internet
Protocol,
we
will
focus
only
on
the
interaction
between
NLSP
and
CLNP
(ConnectionLess
Network
Protocol,
ISO/IEC
8473).
The
network
layer
can
be
divided
into
several
sublayers.
The
amount
of
sublayers
used
and
the
way
these
sublayers
interact
has
much
to
do
with
the
complexity
of
the
interaction
between
different
types
of
underlying
networks.
For
connectionless
communication,
three
types
of
interaction
are
relevant
from
a
security
point
of
view:
- 1.
- CLNP
headers
are
not
encrypted
at
all
- 2.
- CLNP
headers
are
partially
encrypted
(i.e. trusted
domain
addresses
only)
- 3.
- CLNP
headers
are
fully
encrypted
Figure B.3:
Different
locations
for
the
NLSP
layer
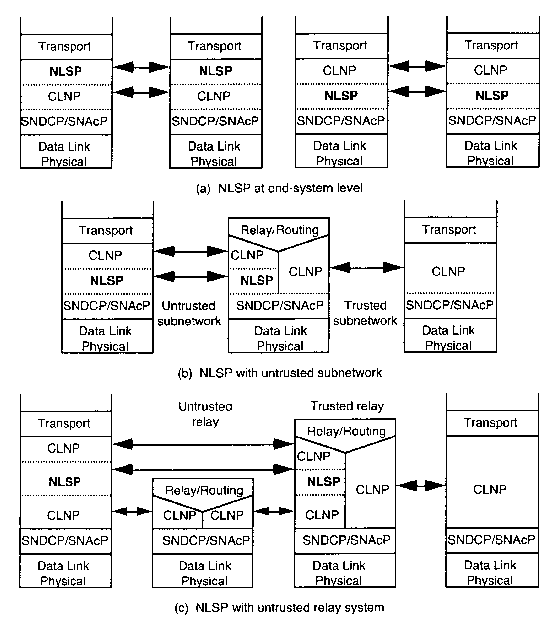
|
The
protection
process
at
the
network
layer
is
much
the
same
as
that
at
the
transport
layer,
but
some
extra
data
has
to
be
added
to
cover
for
services
by
default
not
provided
by
the
network
layer:
- Sequence
integrity
(not
part
of
the
default
network
layer
protocols,
as
opposed
to
the
transport
layer
protocols)
- Traffic
padding
(the
network
has
to
support
traffic
flow
confidentiality,
not
the
transport
layer)
The
security
association
identifier
is
added
in
clear
to
the
secure
network
layer
data
unit.
It
is
interesting
to
know
that
routing
decisions
can
be
affected
through
the
use
of
labels
in
ISO
CLNP
and
Internet
IP
protocols.




Next: 8.3.3 Physical layer security
Up: 8.3 ISO transport and
Previous: 8.3.1 Transport layer security
(c) 1998, Filip Schepers